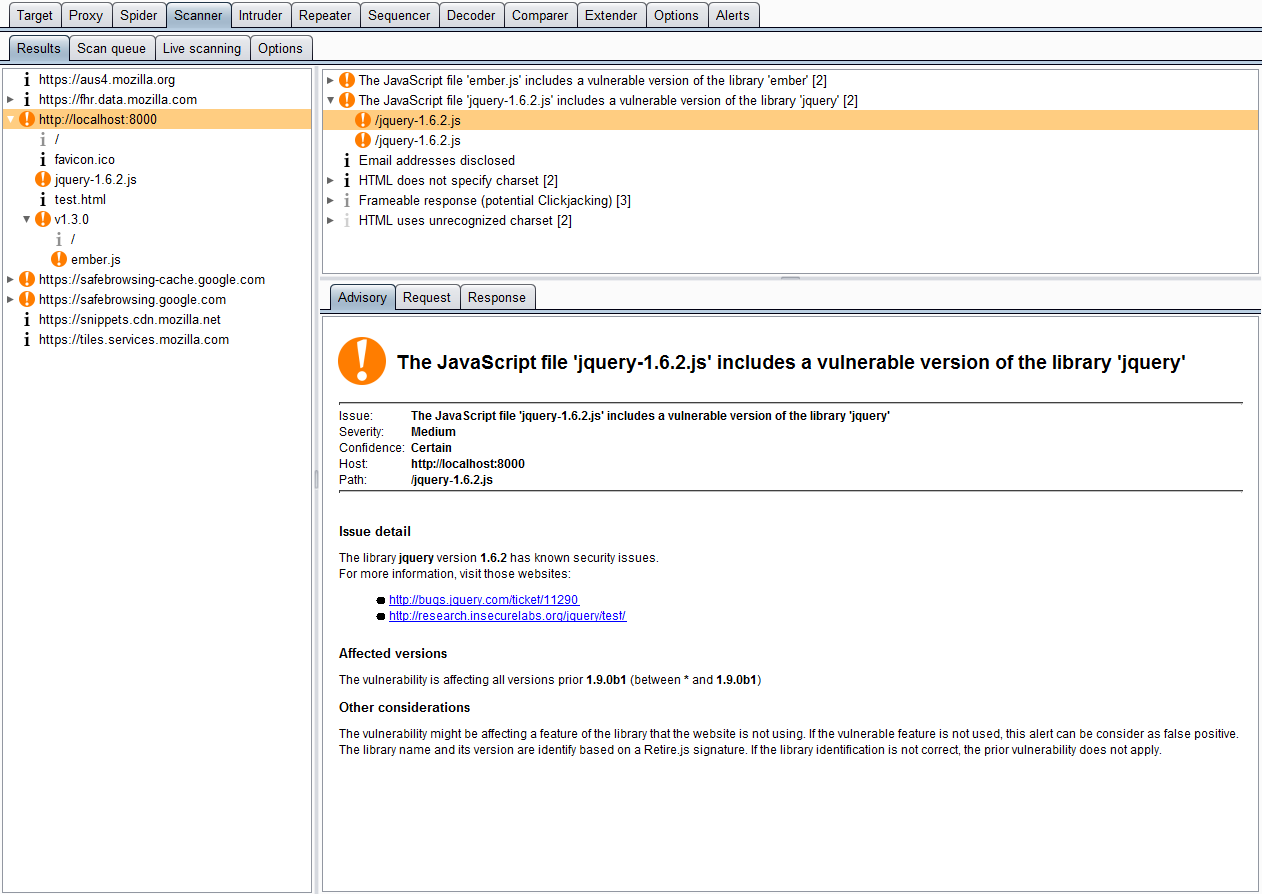
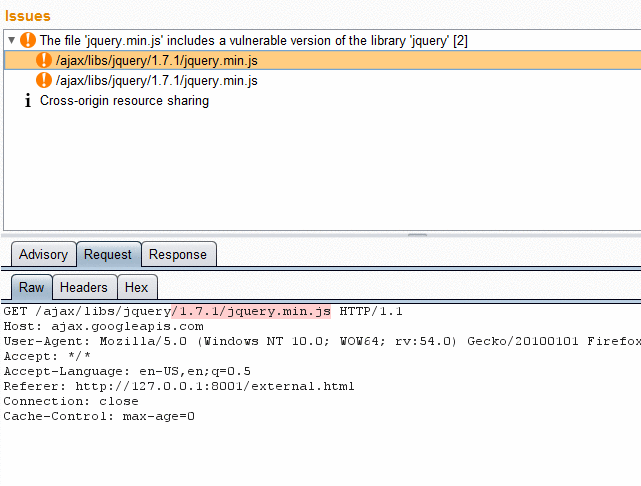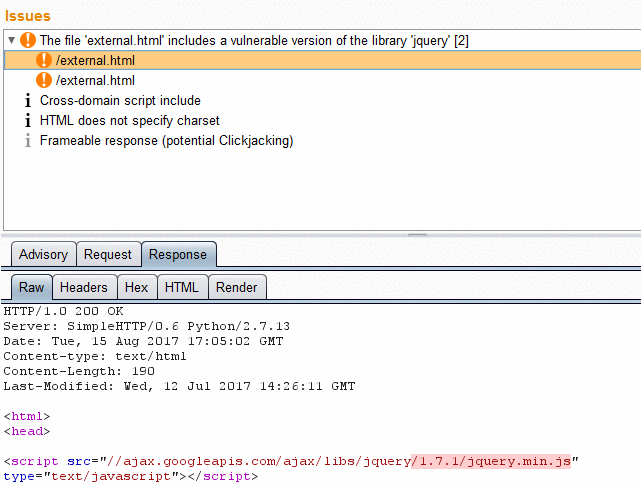
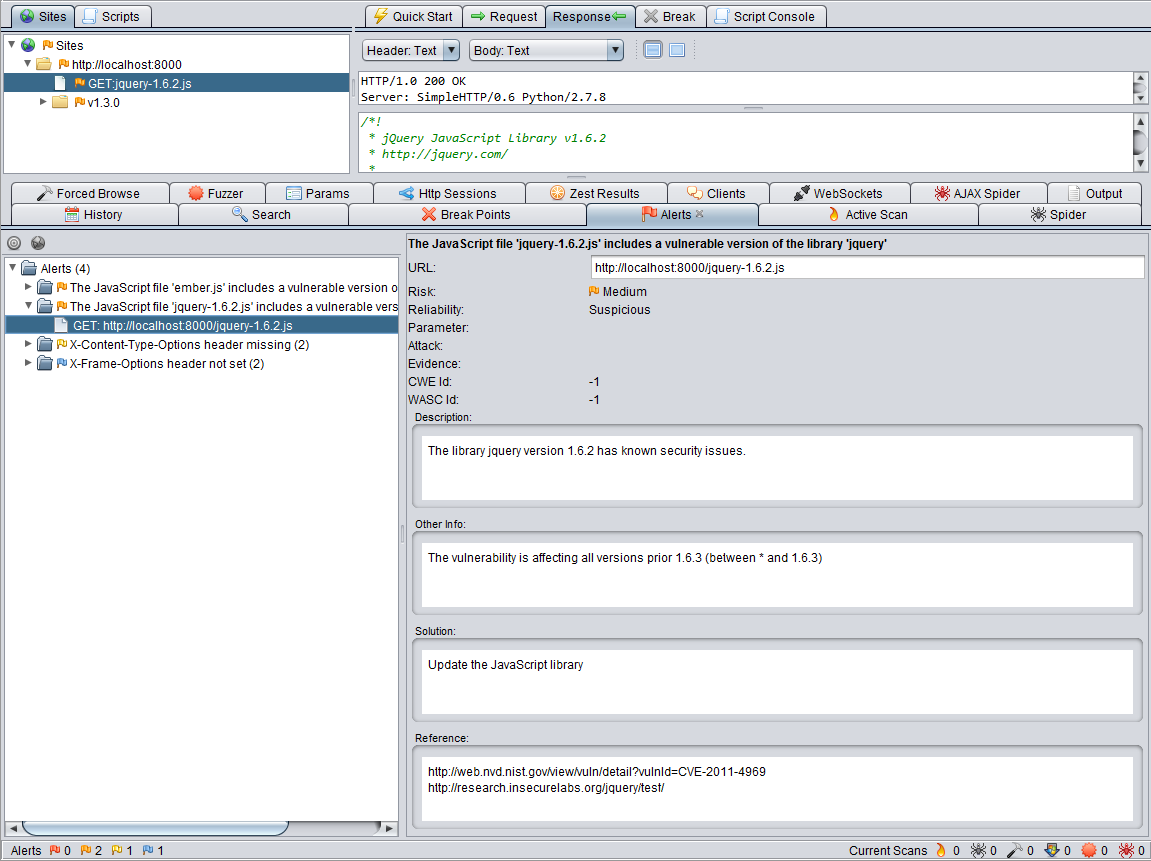
Burp / ZAP extension that integrate Retire.js repository to find vulnerable JavaScript libraries. It passively look at JavaScript files loaded and identify those vulnerable based on various signature types (URL, filename, file content or specific hash).
This software is release under Apache 2.0.
Last updated : December 10th, 2019
Burp Suite plugin : Download (also available on the BApp Store)
ZAP plugin : Download
Run the Maven plugin with the goal scan:
$ cd myproject
$ mvn com.h3xstream.retirejs:retirejs-maven-plugin:scan
[...]
[INFO] --- retirejs-maven-plugin:1.0.0-SNAPSHOT:scan (default-cli) @ myproject ---
[WARNING] jquery.js contains a vulnerable JavaScript library.
[INFO] Path: C:\Code\myproject\src\main\webapp\js\jquery.js
[INFO] jquery version 1.8.1 is vulnerable.
[INFO] + http://bugs.jquery.com/ticket/11290
[INFO] + http://research.insecurelabs.org/jquery/test/
[...]
The additional parameter -DretireJsBreakOnFailure can be use to break the build when at least one vulnerability is found.
[INFO] ------------------------------------------------------------------------
[INFO] BUILD FAILURE
[INFO] ------------------------------------------------------------------------
[INFO] Total time: 1.450 s
[INFO] Finished at: 2015-02-19T13:37:00-05:00
[INFO] Final Memory: 11M/245M
[INFO] ------------------------------------------------------------------------
[ERROR] Failed to execute goal com.h3xstream.retirejs:retirejs-maven-plugin:1.0.0:scan (default-cli) on project
my-web-app: 6 known vulnerabilities were identified in the JavaScript librairies. -> [Help 1]
[ERROR]
Use the following configuration to run the Maven plugin as part of your build. Only one <repoUrl> may be specified at a time.
To scan / iterate earlier in your build cycle, you can bind the plugin to the validate phase.
<plugin>
<groupId>com.h3xstream.retirejs</groupId>
<artifactId>retirejs-maven-plugin</artifactId>
<version>3.0.1</version>
<configuration>
<repoUrl>https://raw.githubusercontent.com/RetireJS/retire.js/master/repository/jsrepository.json</repoUrl>
<!--<repoUrl>https://raw.githubusercontent.com/RetireJS/retire.js/master/repository/npmrepository.json</repoUrl>-->
</configuration>
<executions>
<execution>
<id>scanProjectJavascript</id>
<goals>
<goal>scan</goal>
</goals>
<phase>install</phase>
</execution>
</executions>
</plugin>