My name is Ville Saarinen and I am a passionate programmer from Tampere, Finland.
| Now Playing |
|---|
| Top Tracks |
|---|
🐱 My GitHub Data
🏆 0 Contributions in the Year 2022
📦 49.3 kB Used in GitHub's Storage
💼 Opted to Hire
📜 11 Public Repositories
🔑 0 Private Repositories
I'm a Night 🦉
🌞 Morning 10 commits ██░░░░░░░░░░░░░░░░░░░░░░░ 10.0%
🌆 Daytime 20 commits █████░░░░░░░░░░░░░░░░░░░░ 20.0%
🌃 Evening 69 commits █████████████████░░░░░░░░ 69.0%
🌙 Night 1 commits ░░░░░░░░░░░░░░░░░░░░░░░░░ 1.0%
📅 I'm Most Productive on Sunday
Monday 21 commits █████░░░░░░░░░░░░░░░░░░░░ 21.0%
Tuesday 6 commits █░░░░░░░░░░░░░░░░░░░░░░░░ 6.0%
Wednesday 7 commits █░░░░░░░░░░░░░░░░░░░░░░░░ 7.0%
Thursday 8 commits ██░░░░░░░░░░░░░░░░░░░░░░░ 8.0%
Friday 8 commits ██░░░░░░░░░░░░░░░░░░░░░░░ 8.0%
Saturday 22 commits █████░░░░░░░░░░░░░░░░░░░░ 22.0%
Sunday 28 commits ███████░░░░░░░░░░░░░░░░░░ 28.0%
📊 This Week I Spent My Time On
⌚︎ Time Zone: Europe/Helsinki
💬 Programming Languages:
No Activity Tracked This Week
🔥 Editors:
No Activity Tracked This Week
🐱💻 Projects:
No Activity Tracked This Week
💻 Operating System:
No Activity Tracked This Week
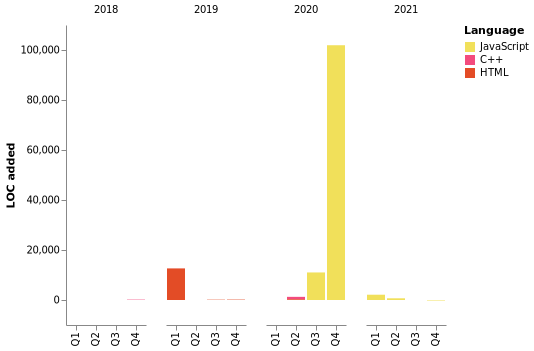
I Mostly Code in JavaScript
JavaScript 5 repos ████████████░░░░░░░░░░░░░ 50.0%
C++ 3 repos ███████░░░░░░░░░░░░░░░░░░ 30.0%
HTML 2 repos █████░░░░░░░░░░░░░░░░░░░░ 20.0%
Timeline
Last Updated on 08/11/2022 18:58:23 UTC
- 🗣 Commented on #251 in vikidi/Homepages
- ❗️ Opened issue #251 in vikidi/Homepages