Important
Powerpipe is now the preferred way to run this mod! Migrating from Steampipe →
All v0.x versions of this mod will work in both Steampipe and Powerpipe, but v1.0.0 onwards will be in Powerpipe format only.
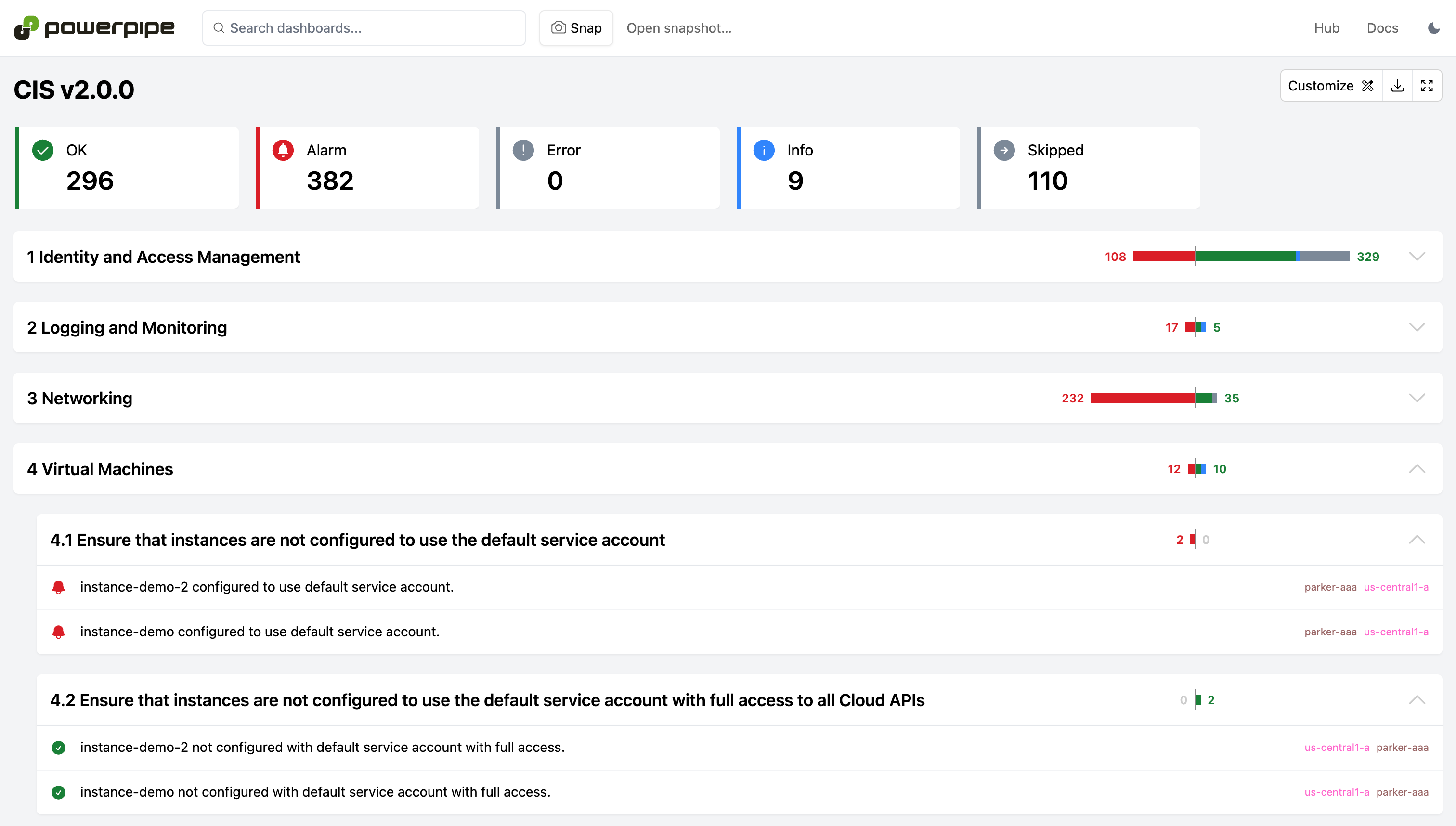
80+ checks covering industry defined security best practices for Google Cloud services.
Includes full support for v1.2.0 CIS, v1.3.0 CIS, v2.0.0 CIS, v3.0.0 CIS, CFT Scorecard and Forseti Security benchmarks.
Install Powerpipe (https://powerpipe.io/downloads), or use Brew:
brew install turbot/tap/powerpipeThis mod also requires Steampipe with the GCP plugin as the data source. Install Steampipe (https://steampipe.io/downloads), or use Brew:
brew install turbot/tap/steampipe
steampipe plugin install gcpSteampipe will automatically use your default GCP credentials. Optionally, you can setup multiple projects.
Finally, install the mod:
mkdir dashboards
cd dashboards
powerpipe mod init
powerpipe mod install github.com/turbot/steampipe-mod-gcp-complianceStart Steampipe as the data source:
steampipe service startStart the dashboard server:
powerpipe serverBrowse and view your dashboards at http://localhost:9033.
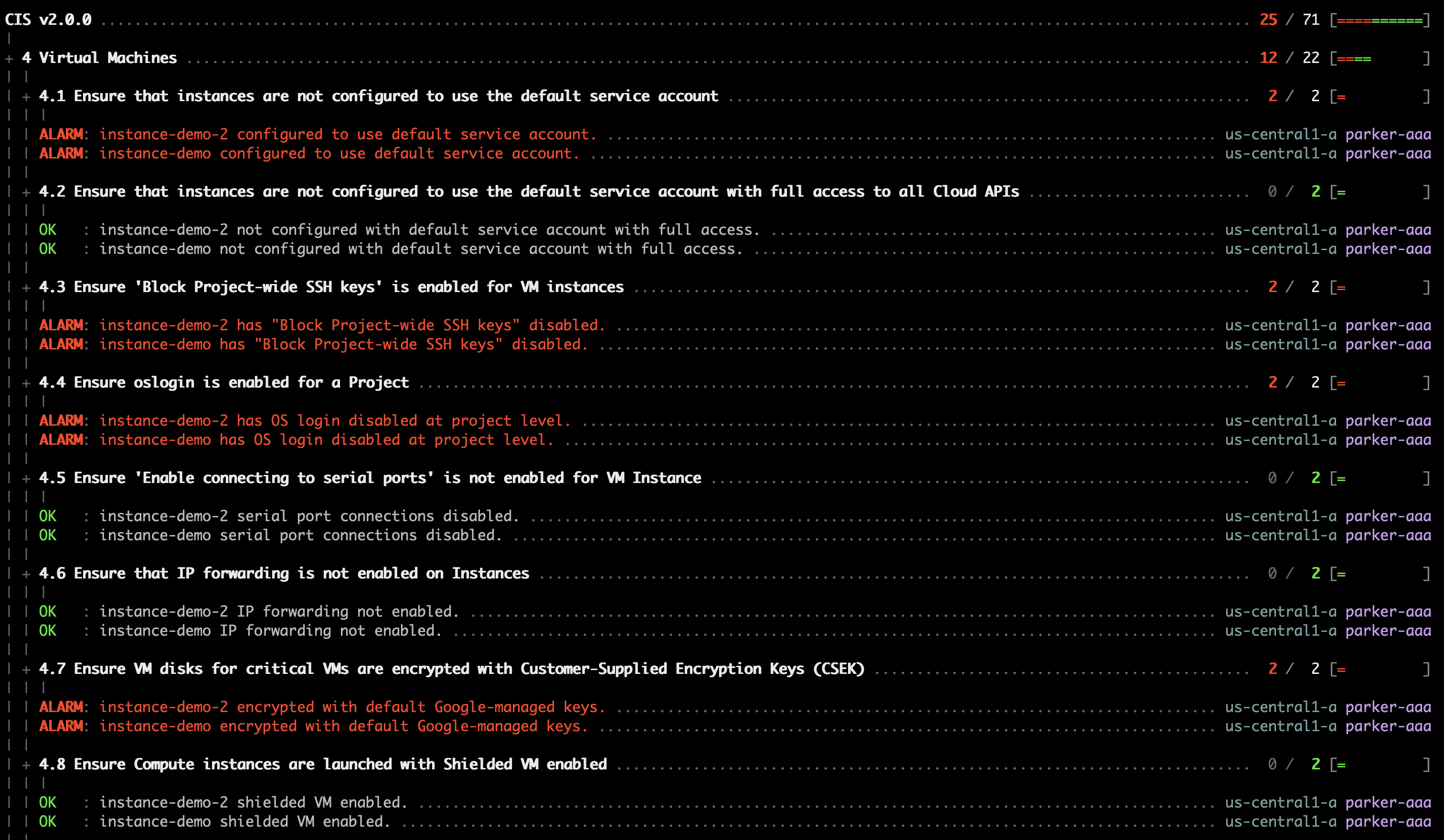
Instead of running benchmarks in a dashboard, you can also run them within your
terminal with the powerpipe benchmark command:
List available benchmarks:
powerpipe benchmark listRun a benchmark:
powerpipe benchmark run gcp_compliance.benchmark.cis_v200Different output formats are also available, for more information please see Output Formats.
The benchmark queries use common properties (like connection_name, location and project) and tags that are defined in the form of a default list of strings in the variables.sp file. These properties can be overwritten in several ways:
It's easiest to setup your vars file, starting with the sample:
cp steampipe.spvars.example steampipe.spvars
vi steampipe.spvarsAlternatively you can pass variables on the command line:
powerpipe benchmark run gcp_compliance.benchmark.cis_v200 --var 'tag_dimensions=["environment", "owner"]'Or through environment variables:
export PP_VAR_common_dimensions='["connection_name", "location", "project"]'
export PP_VAR_tag_dimensions='["environment", "owner"]'
powerpipe benchmark run gcp_compliance.benchmark.cis_v200This repository is published under the Apache 2.0 license. Please see our code of conduct. We look forward to collaborating with you!
Steampipe and Powerpipe are products produced from this open source software, exclusively by Turbot HQ, Inc. They are distributed under our commercial terms. Others are allowed to make their own distribution of the software, but cannot use any of the Turbot trademarks, cloud services, etc. You can learn more in our Open Source FAQ.
Want to help but don't know where to start? Pick up one of the help wanted issues: