discussions's People
discussions's Issues
brr support?
Suggested by @iaMeteor in StreisandEffect/streisand#546
Would you consider to add bbr support for tcp?
ease of install: streisand-builder
One complaint is that it’s still too much of a pain to install Streisand; part of that is the prerequisites. I wrote a cloud-init script that installs them all on Ubuntu 16.04; the script works on Lightsail, EC2, GCE. It is mostly executable as a regular script (as root) on an existing 16.04 box. (It should not regenerate ~/.ssh/id_rsa in that case.)
https://gist.github.com/nopdotcom/032cb37d8a80cb963759baca1ae26755
I think this may be a separate project, say, streisand-builder, to make clear that you don’t get a streisand instance out of it, just a place to stand.
FWIW, Lightsail gets a huge edge here for doing something somewhat evil: it keeps one of your SSH private keys, so it can log you in just with an in-browser terminal. The important part is: You can do a full install without an SSH client, or more importantly, ssh key management.
On Lightsail, the only open ports are 22 and 80. For complete SSH-free operation, we need to fish out generated-docs over port 80.
"Bad encapsulated packet length from peer"
Have installed streisand on a DO server with only OpenVPN and stunnel, when i try and connect with stunnel in OSX i get:
Bad encapsulated packet length from peer (10784), which must be > 0 and <= 1575 -- please ensure that --tun-mtu or --link-mtu is equal on both peers -- this condition could also indicate a possible active attack on the TCP link -- [Attempting restart...]
from tunnelblick.
Any ideas? Should i just try and set up the server again?
Screenshots in generated documentation
Breaking this discussion off from StreisandEffect/streisand#822
Here are my initial thoughts on including screenshots in our generated documentation:
- We now support English and French. I would like to see us add Standard Chinese and other languages to the mix as well.
- It would exponentially increase the scope and difficulty of our translation efforts if we pursued localized screenshots for each of our supported languages.
- That increased effort would combine with other necessary maintenance whenever operating systems are updated and redesigned.
- Screenshots are less accessible for people who utilize screen readers or other adaptive technology.
- We can really easily create custom documentation templates right now that reference a server's IP address and other unique values.
- Screenshots are more difficult to customize, and including static or placeholder values could confuse users.
For now, I think that we're better off sticking with text-based instructions that we try to make as clear as possible. Text-based instructions are easier to update, more straightforward to translate, and age more gracefully.
However, I think it might make sense to include some tiny graphical elements for areas that are really unintuitive (like the OS X VPN icon). These icons don't change as much (the same OS X VPN icon has been terrible and confusing for years across multiple versions) and these elements usually don't include text (which neatly bypasses the translation problem).
Translation "How-to"
Hello,
Thank you for this amazing project. It worked like a charm. Especially if you live country has terrible freedom of speech standards.
My suggest will be to create a how-to about translating "generated-docs" and readme file into foreign languages. I personally would like to translate into my language but couldn't find proper "how to translate" documents.
Doesn't matter for me the skill level of document but "The simpler how-to the more translation" in my opinion.
Update configuration - run installation again
I'm somehow not able to find an answer to my question: How can I re-run the Streisand playbooks on an already configured Streisand VPN server to update the configuration to the latest version without loosing the already available configuration (f.e. client certificates of OpenVPN, etc.)?
Use reduced privilege Amazon user
Suggested by @tomchiverton in StreisandEffect/streisand#461
Right now, the root account's API key is used. Instead the recommendation should be to create an IAM role with just the minimal privileges required.
I don't know enough Ansible to go through and dig out everything the scripts do to produce this list and at least add it to the docs.
There's a starting point shared by @MartinLeedotOrg
Expose onc files for chromebook OpenVpn support
Suggested by @DukeyToo in StreisandEffect/streisand#663
Chromebooks support OpenVPN, but require a onc file to configure it. Those files can then be imported at chrome://net-internals/#chromeos on the Chromebook, according to instructions at https://syedali.net/2014/02/17/using-chromebook-to-connect-to-an-openvpn-server/
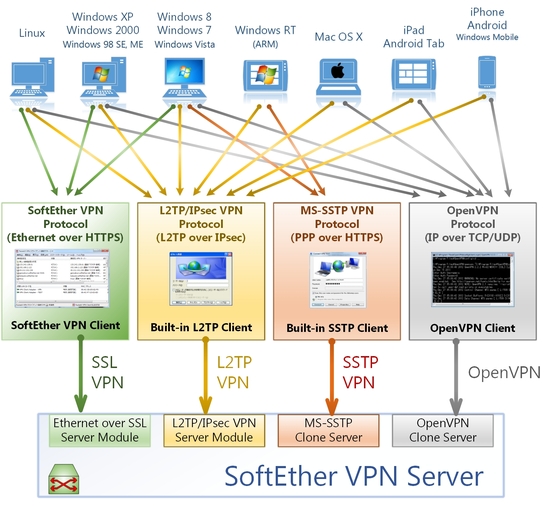
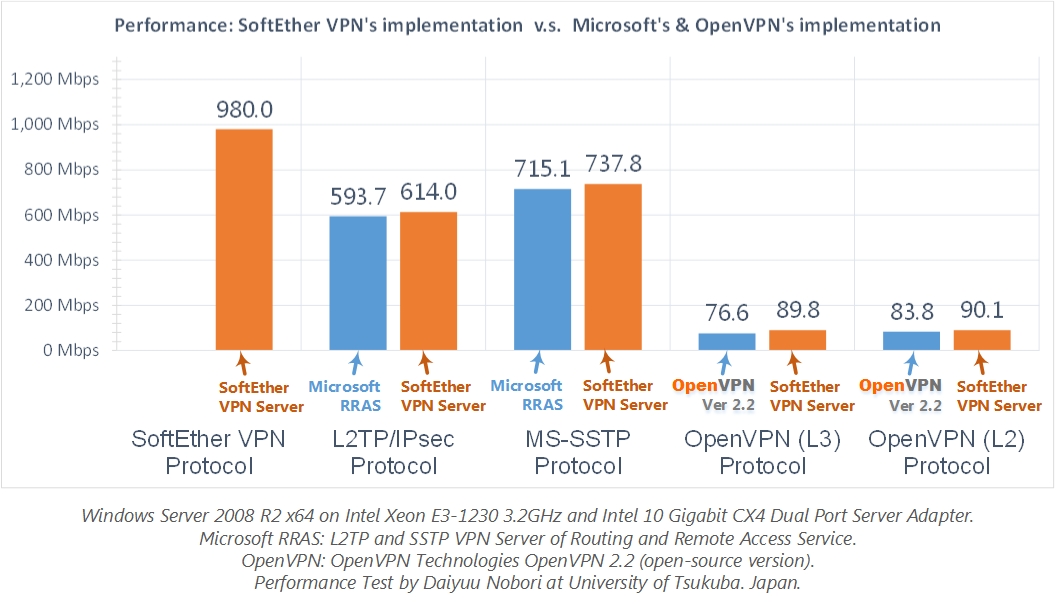
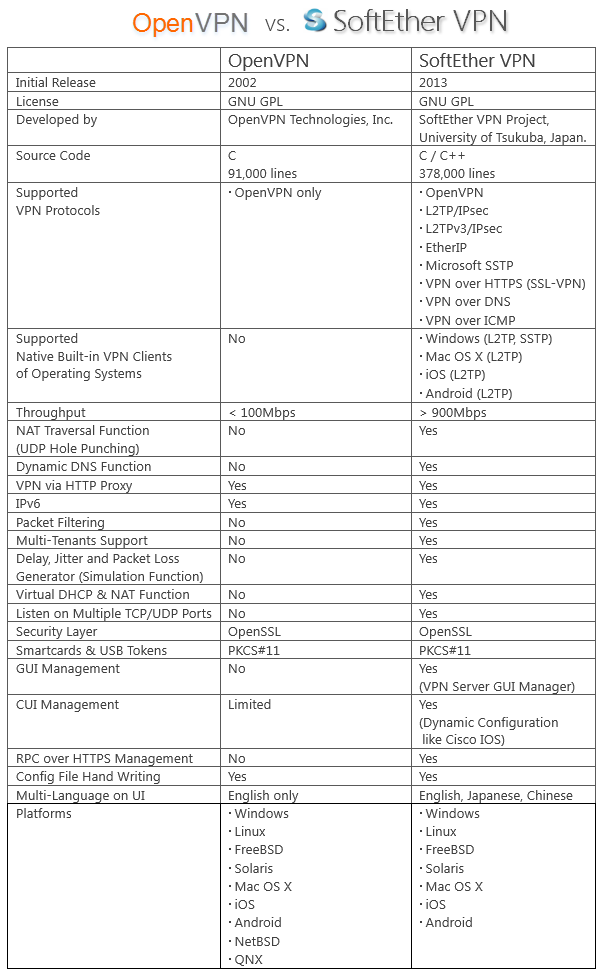
SoftEther VPN
Suggested by @dimzon in StreisandEffect/streisand#140
https://www.softether.org/
It's open source multi-protocol solution, claims is faster than native OpenVPN
Also implements it's own protocol over HTTPSIt will be great to have streisand-like project build on SoftEther VPN
Readme - install dependencies in virtual environment
Suggested by @krzysztofr in StreisandEffect/streisand#8
It is considered good practice to install any external python libraries in the virtual environment (using
virtualenv, docs here), so you don't contaminate your system and have control over the different versions of libraries for different projects.
Such environment could be in any situation easily destroyed and recreated.So, instead of, for example:
sudo pip install botoYou should create and activate virtual environment:
sudo pip install virtualenv
virtualenv venv
source venv/bin/activateand install external dependencies locally, in the context of this environment:
pip install botoMoreover, you can create list of all dependencies:
pip freeze > requirements.txt...and then install them with one command:
pip install -r requirements.txtIf you find my comment useful I can modify Readme file or, if it is needed, provide more detailed explanation.
PRs welcome.
Which dns service is used?
Hi,
This might be a silly question but what dns service is used for Streisand when using Ipsec?
Thanks
OpenVPN instructions don’t steer to UDP first
UDP OpenVPN is superior for performance. Should we recommend the UDP/combined profiles, with TCP as a fallback?
I honestly don’t know if emitting OpenVPN UDP packets will cause unwanted attention.
[feature request] including ZeroTier
Suggested by @strixaluco in StreisandEffect/streisand#390
Wanted to suggest ZeroTier, which is zero-configuration multiplatform software-based FOSS switch.
Technical FAQClients:
ZeroTier One
Linux / macOS / Windows / Android / iOS
[Feature Request] Add traffic optimization software to boost the speed
Suggested by @HowardMei in StreisandEffect/streisand#723
There are several traffic optimization suites good for speed:
Server & Client: kcptun
Server Side: TCP BBRCould we have them as an option please?
Feature idea: nghttpx for HTTP/2 proxy
Hi,
I am both a big fan of Ansible and all kinds of VPN / proxy software. So I am thrilled to find such a awesome, detailed documented project like Streisand.
I am thinking about contributing a new Ansible role to Streisand that sets up an nghttpx HTTP/2 proxy.
HTTP/2 proxy is, in fact, a secured forward proxy that can only be used natively by modern browsers like Chromium / Google Chrome and new versions of Firefox. Using the proxy in other software is possible with additional client software.
Plain HTTP forward proxy has been blocked decades ago in China, but by wrapping an HTTP proxy in a TLS connection you get an HTTPS proxy. There are many ways to do it:
- Setting up a plain HTTP forward proxy like Squid and wrap the connection with stunnel;
- Compile Squid with
--enable-ssl(non-default for most distros) and it can serve HTTPS proxy natively; - Setting up an nghttpx daemon that translates between HTTP/2 and HTTP/1.1, acting as a frontend to an HTTP/1.1 forward proxy like Squid. Since modern browsers support only encrypted HTTP/2, this method is secure by default.
The last method has the best performance thanks to HTTP/2.
A few considerations:
- Authentication could be done during TLS handshake, or via HTTP basic auth (encrypted in TLS), or both. I prefer the former one but this requires manually importing a client certificate to the browser. What's your opinions?
- The biggest disadvantage of this method is that you need a valid HTTPS server certificate for your HTTPS proxy, just like any HTTPS website. The difference is that there is no "Proceed to XXX (unsafe)" link to click on and ignore the security warning. There is only an
ERR_PROXY_CERTIFICATE_INVALIDerror which cannot be dismissed. So self-signed certificate simply does not work. Should the playbook prompt for a valid HTTPS server certificate to copy to the remote server?
Add Privoxy support to weaken mass data collection
Suggested by @DanielHeath in StreisandEffect/streisand#62
If we're trying to prevent/avoid mass data collection as well as mass censorship, www.privoxy.org or similar might be a worthwhile addition to the streisand bundle.
Any interest? I might see if I can get it running next weekend.
There was some follow-on discussion in StreisandEffect/streisand#62 that should be referenced by anyone wanting to restart the discussion here.
Windows provisioning support
From Jim Salter:
First gripe - you can't run the initial setup on a Windows machine.
While likely low on the priority list this issue captures this feature request. It seems there is some Ansible support and with the newer "Windows subsystem for Linux" it might not be as hard to implement as it was at the time Streisand was started. Alternatively: perhaps there's a way to provide a VM/docker image.
What are the relative costs of cloud providers?
People who post here generally know what the pricing is like for various cloud providers. But it’s not obvious to new users how to choose a vendor that best fits their needs.
We can’t document every provider in the world, so I think they’re not eligible unless they have specific support in Streisand. For now, I think it’s fine to be US/EU-centric. Here’s a rough sketch:
(failtable moved to next comment)
Move streisand to a pip package
Suggested by @mcginty in StreisandEffect/streisand#1
Is it possible to move streisand to a pip package and include boto/dopy/etc as dependencies to help it run out of the box? Or maybe make a PPA/brew to include ansible too?
Automatic IP rotation?
Suggested by @tedd4u in StreisandEffect/streisand#792
I have to manually rotate IP addresses today which is time consuming and no fun.
Expected behavior:
Streisand automatically rotates apparent external IP every X minutes.
Actual Behavior:
No rotation.
Clarified with:
Yes - I was completely vague. I guess what I want is to have the instance retain the same IP (call it address A) for OpenVPN access, but to use a different IP (address B) for outbound / upstream traffic. Further, I'd like address B to change periodically. Like every 30 minutes or something. Cycling through new ephemeral IPs.
I guess the argument could be made that I should just use tor, but that's a
big price to pay.My application is anti-tracking/profiling, not anti-surveillance.
Maybe there are other options?
Feature request: Add script function to destroy running cloud instances
From @andrewcockerham in StreisandEffect/streisand#798:
I just want to suggest the feature of a simple part of the ./streisand script that would allow you to shut down running EC2 instances. I fired up a VPN, for a few days, but then stopped using it. At the end of the month I got a bill from AWS because I had left that instance running non-stop for the whole month, even when I wasn't using it. Would be great to 1) have a way to shut it down through the ./streisand script (rather than having to go to AWS console), and 2) even better would be a way for streisand to automatically shut down any running instances when I stop using the VPN on my mac. Don't know if that's possible?
[Request] Add in DNS encryption.
Suggested by @Rich700000000000 in StreisandEffect/streisand#272
First of all, this is an excellent project: We need more automatic tools like this. However, you're still missing one critical tool: DNS encryption.
Even if you're using TOR or a VPN, your DNS queries are still sent to the server in cleartext. And worse, it's usually google's dns server at 8:8:8:8. If we added in DNScrypt, using the server version they have available, that would go a long way towards eliminating a possible weak link.
Mirroring documentation
We already mirror software packages because our users don’t have Internet access (yet). Is there non-Streisand HTML documentation we should be mirroring as well?
(I can’t think of any examples now, except maybe the OpenWrt how-to.)
Create new server with previous gateway passphrase
If I have a Streisand instance running at https://poem-walk.example.com, it isn't really that bad to replace it with a new instance if I can change where that DNS name points, right?
For the server owner, the hardest part is the disseminating the new passphrase. (It would be nice to have (at least) LE cert continuity too.)
If users have the passphrase, they can hit the new gateway to pick up new configuration. Reconfiguring their services can be easy or hard, depending on which VPN they're using on which client OS. OpenVPN users can grab a new config file; iOS/macOS users grab a new mobileconfig. (I'm working on Windows.)
All I need is a way of deploying with the same passphrase.
I want to discourage people from choosing passphrases, so I'd prefer the input to the later run to be in some opaque/ASCII-friendly form, like base32, or the binary version of BIP passphrases. It's just there to slow people down; anybody who wants a weak passphrase that much can have it, with or without our help.
Amazon Lightsail
Suggested by @ptm2x1NyqFB2RY in StreisandEffect/streisand#483
Amazon has introduced new VPS with flat rate pricing. Worth considering as a new provider?
RFE: Use terraform to access multiple provider apis from a single library
Vagrant usage fails, is lacking documentation on key organization
Host system: Ubuntu 14.04, Ansible 2.4.0.0.
Jumping in fresh to look at Streisand, my expectation was that I could just launch the streisand-host Vagrant guest and start poking around. Sadly, vagrant up streisand-host just fails outright on the absence of a key.
PLAY [Prepare the vagrant VM for Ansible] **************************************
TASK [Gathering Facts] *********************************************************
ok: [streisand-host]
TASK [validation : Stat the Streisand SSH private key] *************************
ok: [streisand-host]
TASK [validation : Fail if the Streisand SSH private key file doesn't exist] ***
fatal: [streisand-host]: FAILED! => {"changed": false, "failed": true, "msg": "The Streisand SSH private key \"~/.ssh/id_rsa\" does not exist."}
So for the purposes of just getting it to work, I could:
mkdir ssh-keys
ssh-keygen
to put an id_rsa into a directory in the project, then map it in the Vagrantfile:
streisand.vm.synced_folder "ssh-keys", "/root/.ssh"
This appears to get the job done, as would the dangerous choice of syncing my ~/.ssh:
streisand.vm.synced_folder File.expandPath("~/.ssh"), "/root/.ssh"
None of this is mentioned in the Streisand testing docs, however ( https://github.com/StreisandEffect/streisand/blob/master/documentation/testing.md ) which give the impression that all you have to do is fire up Vagrant and off you go.
How are the developers working with this? What is the preferred fix here?
How much work to run in an LXC container?
What will be broken in running a live system in an LXC container? Pure userland stuff like shadowsocks should work anyway.
Do the recently-disclosed dnsmasq vulns need to be addressed?
Right now it looks like streisand boxes are using a vulnerable version of dnsmasq. Version 2.78 is the latest and includes a lot of security fixes. I see 2.75 on my streisand instance. Would there be a way to address this soon?
shadowsocks traffic detection
@OneHappyForever asks in StreisandEffect/streisand#501:
Hi,
Just wanted to know what you guys think of the shadowsocks traffic detection apps made available by shadowsocks and shadowsocksR developers. Do you think they point to possible weak points and areas of imporovement?
Here are the links:
https://github.com/madeye/sssniff
https://github.com/breakwa11/shadowsocks-rss/issues/868
IPSec IKEv2
Suggested by @chenhouwu in StreisandEffect/streisand#110
Would like to have support of IPSec without l2tp.
l2tp is blocked often by GFW,
I hear that IKEv2 is never blocked.
There is some substantial follow-up discussion from @jlund and others in StreisandEffect/streisand#110 that should be referenced by anyone wishing to restart this discussion here.
Should users have to visit our web server?
With fancier client installation methods on the horizon, should we still expect users to visit our HTTPS server first?
Apple mobileconfig profiles can contain multiple payloads. The bare-mobileconfig branch is called “bare" because it only ships a VPN definition. A mobileconfig could also ship the server SSL certs more conveniently than the current method. (The cert mobileconfig would be a data: URL in streisand.html.) While we’re at it, we can also deploy client SSL certs, if we wanted to authenticate clients that way.
The fastest path to an automatic Windows L2TP setup tool may be either an NSIS “installer” (which would be generated for each Streisand server) or PowerShell. These too have a chance to drop SSL certs on the machine.
So for some users, the web site may be just a speedbump to getting to the juicy mobileconfig/installer files inside. Instead of sharing streisand.html, they could share the config files instead. But is that a good behavior to encourage?
One path to server migration is to post instructions on old-streisand (#30) but if users can’t/won’t visit https://old-streisand, then instructions there won’t help.
Planned migration tools
I think there’s also a need for user-visible machine inventories, but different issue.
Often, you know in advance that you’ll be migrating Streisand services from one host to another. Some people trust the integrity of Streisand-hosted HTTPS more than they trust the method they will use to get their streisand.html files.
It would be nice to have a way to put a banner on the web server: “This server is moving. Click here for the new certificate and connection instructions.”
For new servers, what you’d really like to do is notify VPN users of the upcoming change when they connect to old-streisand. I don’t know if this is possible for any or all services.
US-centric use case: evil ISP, high bandwidth, low expectations
Warning: contains out-of-scope material
I am writing this down because I don’t want to forget it. The solutions look beyond streisand’s scope, although they may affect how some things are done. This is back-burner.
2017: Everyone won’t outrun the bear
There’s an old joke that if two people are being chased by a bear, the winner doesn’t have to outrun the bear to survive; she just has to outrun the other person.
I’ve had a number of people ask me about things like the EFF’s advice on protecting yourself from your ISP. I think there’s an intermediate use case for people who can’t/won’t run all their traffic through a VPN.
Outrun something
Mitigations in rough priority order:
- Stop using your ISP’s DNS resolvers. They are just too easy to log.
- HTTPS Everywhere.
- Privacy Badger/uBlock Origin
From here, we get into counters for blackhat DPI/M crap:
- Encrypt your DNS requests to your private resolver. No sense in making life easy for sniffers.
- Force port 80 traffic over the VPN. We know it’s cleartext.
- ...to clean up after that, you may need a whitelist for 80. Many services (hi, Netflix!) will pick an edge server close to where “you” are. This especially sucked when my IPv6 address lived elsewhere, and I got a strange geographical mix of edge servers.
- ...and after the port 80 whitelist, you want a list of sites never to visit over a non-VPN connection?
What’s not being mitigated:
- SSL destination IP/port. Well, you said you didn’t want to run everything over a VPN; this is the price.
- Tracking on HTTPS pages via page content. Not as much of a worry with regards to your ISP, and uBlock Origin is the best I can think of.
- BitTorrent. Somebody who knows BT hygiene can write that.
- Traffic analysis. Your ISP knows when you are sleeping, they know when you’re awake.
- Things I can’t come up with in the morning.
Approaches
I speak LEDE, so everything looks like a $20 nail.
Somebody brought up Raspberry Pis--they have bad network performance, but they’re available everywhere, and their entire state is stored on a microSD card. The boot partition is FAT32. Most people could edit a text file on the microSD card on their main computer for initial IP configuration. Something like the RPi0 or related embedded computers may become very popular given the recent news about Apple’s App Store. (Please don’t ask here what I mean.)
document that we have a tree of certs
I expected the cert in streisand.html to be the cert used for the website (and in fact all other server identity). I wasn’t expecting the streisand.html cert to be a root for the use-certs.
I think leaving this undocumented in streisand.html will complicate the ability for users to get local support; I know I misdiagnosed some problems based on that faulty assumption.
Streisand Share Network
Finally just got this setup and using just the OpenVPN config so far. I'm using a MSDN Azure cloud tied to an identity.
Upon first connection, noticed that both Amazon and GMail didn't 'trust' me and required 2FA.
There goes my anonymity - the analytic networks are too advanced to hope this doesn't get passed on to other collectors. And I'm sure it's worse in places like China, Iran, etc.
What's something we can do to create a peer-to-peer / share network of Streisand servers with minimal setup? We need some sort of trust-ring to avoid signing into the same VPN server, possibly via a proxy from our static server.
Or is this what TOR is supposed to accomplish? I'm not yet familiar with that, and will take a look.
Integrate Pi-Hole?
It would be great if Streisand can integrate https://pi-hole.net and block all ads on internet :)
QNAME minimization, replacing dnsmasq with Unbound
Suggested by @L-P in StreisandEffect/streisand#459
Hi,
QNAME minimization (RFC 7816) is a way to resolve domain names without having to send the full request to every authority in the chain. ie. if you have three authorities, A knows who has
.com, B.foo.com, and Cbar.foo.com, you ask A for.com, B forfoo.comand C forbar.foo.com, instead of leaking the fullbar.foo.comto everyone.I think this would be a privacy improvement and is quite cheap to implement.
dnsmasq is currently used as a DNS resolver, I propose to replace it with Unbound as it implements QNAME minimization.
From the package description:
Unbound is a recursive-only caching DNS server which can perform DNSSEC
validation of results. It implements only a minimal amount of authoritative
service to prevent leakage to the root nameserversFreeBSD considered it stable and secure enough to replace BIND in 2014.
Replacing dnsmasq with Unbound should be painless, migrating a live server could be doable by downloading the unbound package before removing dnsmasq. I don't know if such a migration should be included in Streisand as it will be dead code as soon as gets written.
TL;DR questions:
- QNAME minimization, yay or nay?
- Is it worth replacing Dnsmasq ?
- Should an automatic dnsmasq->Unbound migration be included in Streisand?
AWS blocks the use of its VPS as VPNs from China
I thought this news might be relevant here.
https://www.reuters.com/article/us-amazon-china-vpn-idUSKBN1AI0CM
Now China users are one provider short.
[Suggestion] Mirroring 'SSLDroid' and 'OpenVPN for Android' apk files
Suggested by @Denoza in StreisandEffect/streisand#268
Hi,
In countries where Google Play Store is blocked, it could be pretty difficult to obtain apps like 'SSLDroid' and 'OpenVPN for Android' esp. under tightly restricting conditions. I think it will be a good idea to mirror them on the streisand host server upon setup. Just a suggestion for the sake of further betterment.
Shadowsocks method chacha20-ietf-poly1305 not supported
I can't make any shadowsocks client on Ubuntu 16.04 run connect to streisand with method chacha20-ietf-poly1305. I always get this
chacha20-ietf-poly1305
I updated my shadowsocks-libev to 3.0.8, which should have solved this problem as this method is supported since version 3, but to no avail.
So, my question is can I change the method on my streisand-server post- or pre-installation?
Feature: DNS instances
I think it would be useful and more secure to have a way to create DNS instances that are secure and log no information. The VPN instances would then use these for DNS instead of Google or whatever it currently uses.
Feature Request: Add destruction capabilities
Suggested by @MarinLeedotOrg in StreisandEffect/streisand#475
For those unfamiliar with AWS, removing the created instance might be a bit tricky, this could be automated.
I've created a destroy branch at: https://github.com/MartinLeeUK/streisand/tree/destroy
Before I submit a pull request, is this needed? Is there a better approach?
A request for Docker Image
Suggested by @aminbolehvpn in StreisandEffect/streisand#126
Hi Joshua,
Is it possible to have docker images? It will do the deployment of streisand a lot quicker to novices.
There was some follow-up discussion in StreisandEffect/streisand#126 including links to docker-streisand projects others have put together that should be referenced by anyone wishing to restart this discussion.
Also an older PR: StreisandEffect/streisand#442
Feature request: User management / Access revocation
Suggested by @stevekuato in StreisandEffect/streisand#235
I guess this is a question more than a feature request.
How would I go about revoking access to someone who I previously sent the HTML instructions to?
Is there a process for this? (e.g. regenerate the passwords + HTML file.)
Thanks.
Docs: distinguish the machine building a streisand server from the server itself
I’m running into documentation problems where I need to distinguish the place ansible is being run, and the deployed server.
I am planning on naming the ansible machine as the Streisand builder, and the deployed server the Streisand server.
Please keep bikeshedding to one per person. (I’m joking, I don’t care.)
FYI: ShadowVPN
Suggested by @dimzon in StreisandEffect/streisand#142
Yet another lightweight VPN protocol for low-end devices (routers etc)
https://github.com/clowwindy/ShadowVPN
https://github.com/clowwindy/ShadowVPN/wiki/Compared-to-Shadowsocks-and-OpenVPN
Would our own DNS resolver help? With anything?
Which DNS server do we use? Well, we can use our own. I suppose it depends on your estimates of risks of DNS-lookup logging versus flow sniffing/logging.
The unbound package is available for Ubuntu.
Unbound is a recursive-only caching DNS server which can perform DNSSEC
validation of results. It implements only a minimal amount of authoritative
service to prevent leakage to the root nameservers: forward lookups for
localhost, reverse for 127.0.0.1 and ::1, and NXDOMAIN for zones served by
AS112. Stub and forward zones are supported.
GoVPN, Vpn-WS
Suggested by @gsdu8g9 in StreisandEffect/streisand#536
The author of govpn said that it works in China.
http://www.govpn.info/Modes-of-operation.html
https://github.com/stargrave/govpn
Also this vpn looks interesting.
But I am not sure that it will work everywhere.
https://github.com/unbit/vpn-ws
redeploy server with new public IP
Suggested by @nickolasclarke in StreisandEffect/streisand#184
First off, this is more of a troubleshooting issue than an actual bug, and I do not think this is the most appropriate place for a discussion, but alas, it seems this project does not have a IRC/gitter/mailing list so I'm dropping my problem here. I am currently based in China and I am waging a constant battle against the GFW. While it is hard to confirm definitively (given that results are sporadic on a day to day basis) I believe that often my connections to my streisand instance, no matter what protocol or solution I use, after a few days or even hours get blocked.
For example, right now, while I can SSH to my streisand instance by IP from a jump host and get 0% packet loss from a ping to it from that host, I get around 75% packet loss from my desktop and cannot connect over L2TP/IPSEC or use shadowsocks. However, from my phone I can still successfully connect to the server. While this is not definitive proof, given the constant issues I have with different connections at different locations, I am fairly confident that this is more than simple connectivity issues and is directly related to connection sabotage. the GFW is wildly inconsistent and it is hard to nail down exactly what is causing what.
So, one solution I have found is to simply take a snapshot of a streisand host (I am currently using Digital Ocean Singapore) and then whenever my connection seems to have permanently degraded, I spin a new droplet from the snapshot, modify a few configs files by hand, (such as /home/shadowsocks/config.json:$SERVERVAR) and point my clients at the new IP. This saves having to spin a whole new instance each time, and heavily modify all my client configurations and also seems to fix, albeit temporarily, the problems at hand.
However, I am have not had luck getting l2tp/ipsec to work with this solution, and I have also noticed that the webserver does not seem to be working either. I was hoping to get some help identifying all the requisite configurations that should be modified in order to support a public IP migration since this is the first time I have worked with many of these technologies before. Once I've nailed down the process by hand, I plan to write a tool to quickly redeploy a configured Streisand DO droplet with a new IP which I'll gladly publish here on github.
If there is a better place to publish requests such as these in the future, please let me know and I'll move this to the appropriate forum.
On a related note, being able to backup the full set of Streisand configs and feed them into a deployment would be a great feature, but is outside the scope of this initial request, but I thought I would plant the seed :)
Recommend Projects
-
 React
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
 Typescript
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
-
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.