This public repo serves the Azure Monitor community. It contains log queries, workbooks, and alerts, shared to help Azure Monitor users make the most of it.
Queries - copy and paste queries to your Log Analytics environment, or run on the Log Analytics Demo Environment
Workbooks - the workbooks in this repo can be deployed as ARM templates to your Azure Monitor environment
Alerts - the alerts in this repo are log-based, meaning they are in fact log queries. You can run them on the Log Analytics Demo Environment or use them to create and test alerts on your own environment
Anyone can contribute to the repo, you don't need to be a pro. Have an interesting query or workbook? fork this repo, add your content to your fork and submit a pull request. See Contributing for more details.
The October top contributor is ![]() Bruno Gabrielli (Brunoga-MS). Thanks Bruno!
Bruno Gabrielli (Brunoga-MS). Thanks Bruno!
Great workbooks were added, such as AntiMalware Assessment and Azure Inventory (based on Azure Resource Graph), as well as a lot of new queries for many Azure services. For more details see our Wiki.
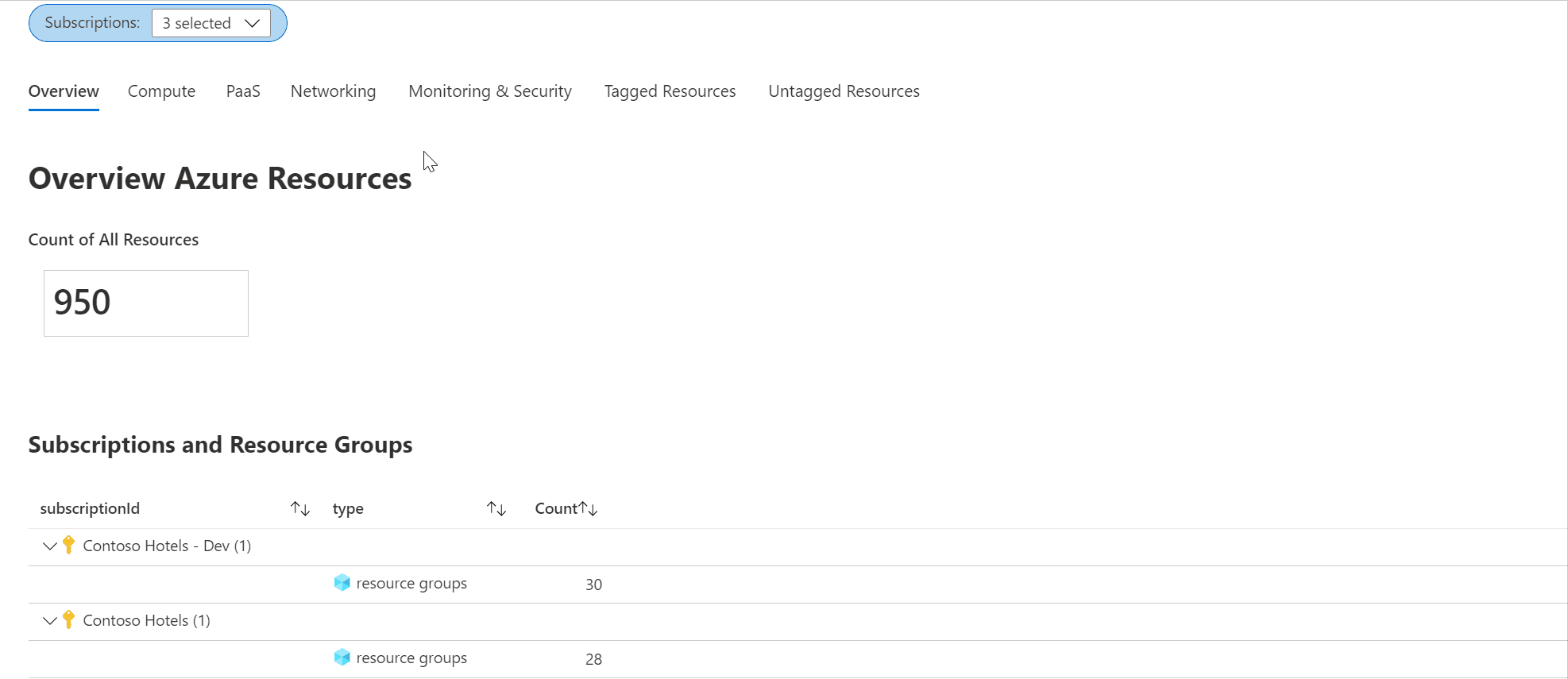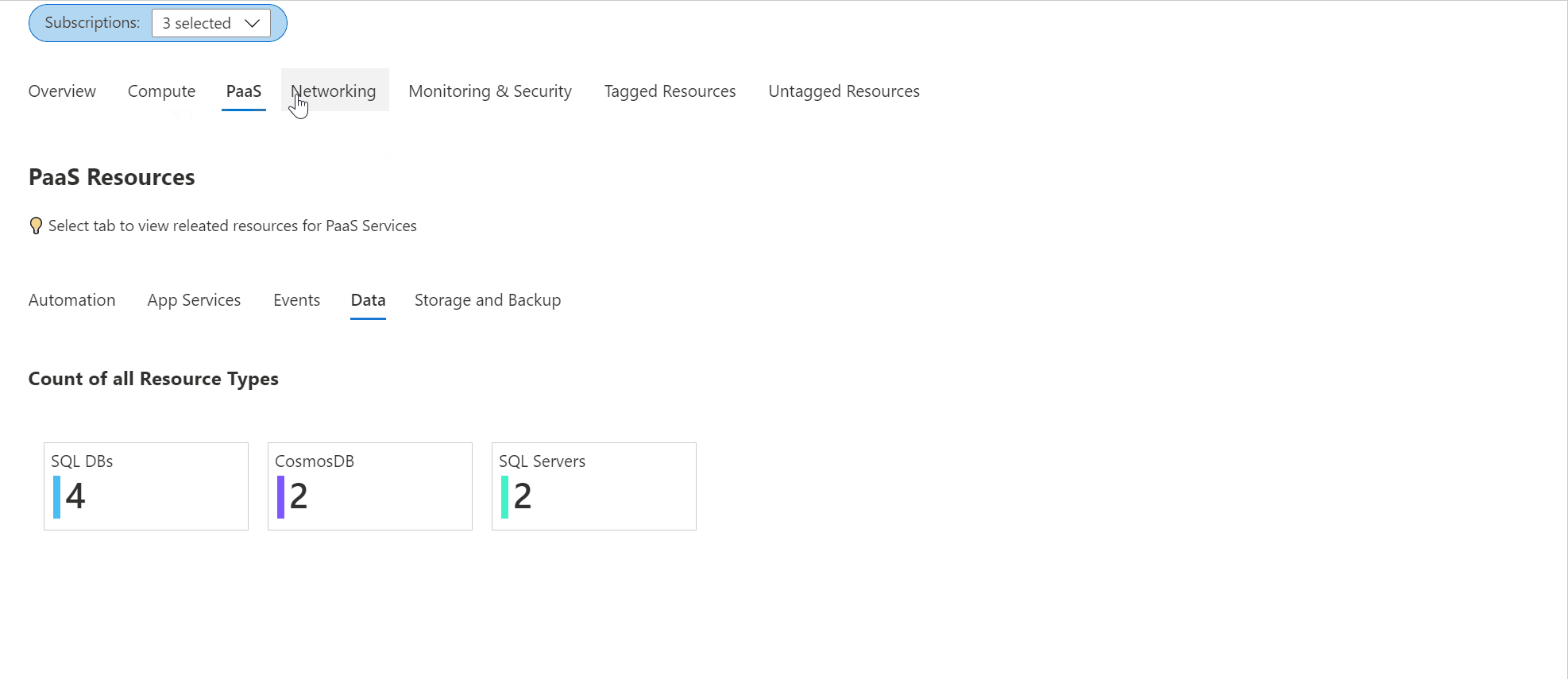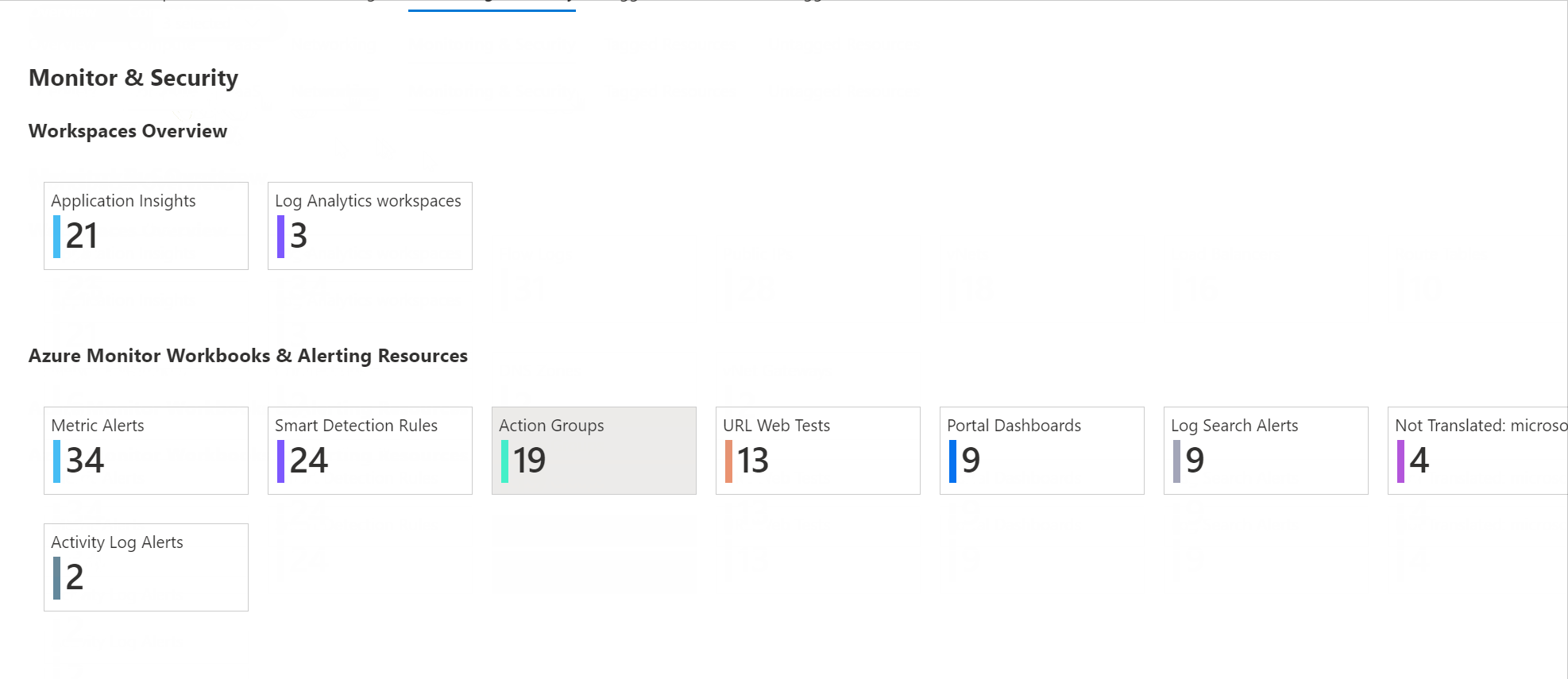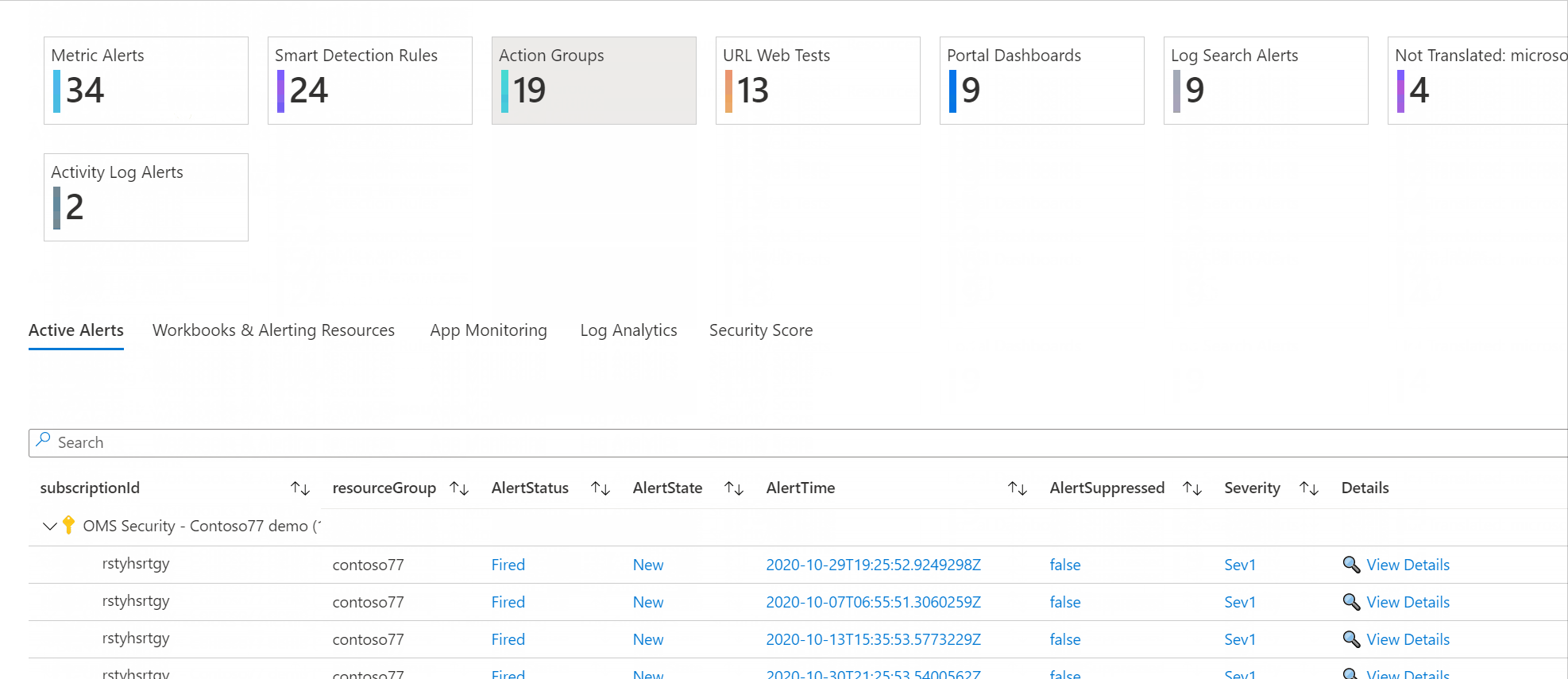
Check out the Azure Inventory workbook (based on Azure Resource Graph)
and the AntiMalware Assessment workbook
Here are some ideas on what other users are looking for.
| File/folder | Description |
|---|---|
Azure services |
Queries, workbooks and alerts for specific Azure services |
Scenarios |
Queries, workbooks and alerts to handle common "How to's |
Solutions |
Queries, workbooks and alerts organized by solutions |
CONTRIBUTING.md |
On how to contribute to this repo |
LICENSE |
The license for this repo |
README.md |
This README file |
The content in this repo uses KQL (Kusto Query Language). To get started with queries see this article.
This repo has many examples that you may want to edit to fit your exact scenario. If you're not sure how to do that - post your question on our community forum.
Use Issues to call us out on missing content or something else we should improve on, and check out the FAQ page for common questions & answers.
Upon redistribution of this repo, please be respectful of the readers and authors of this documentation, and include a link to the original repo master branch.