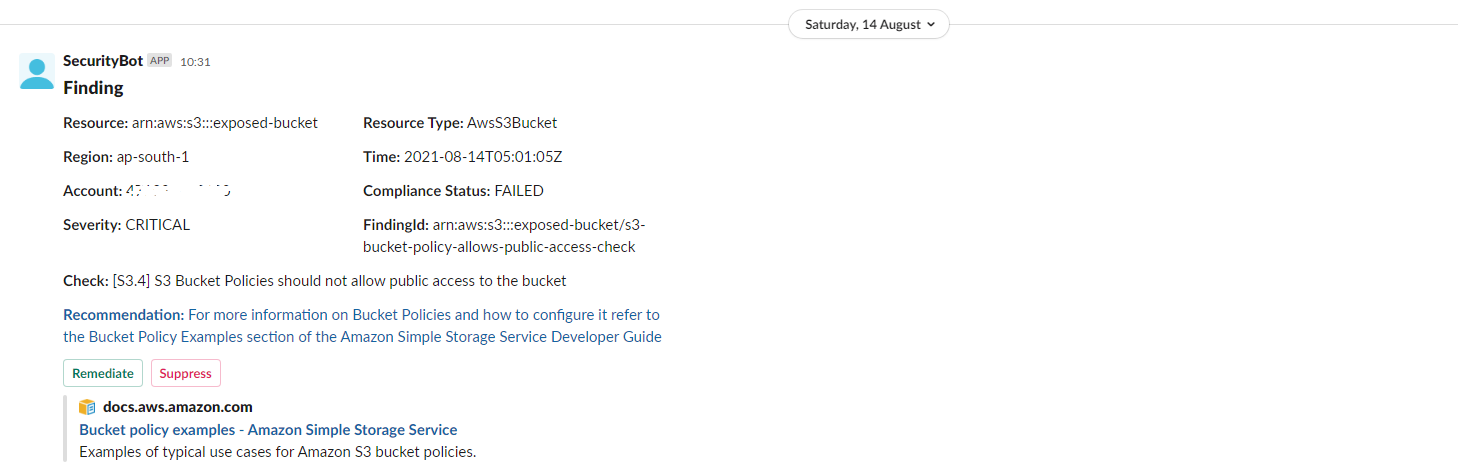
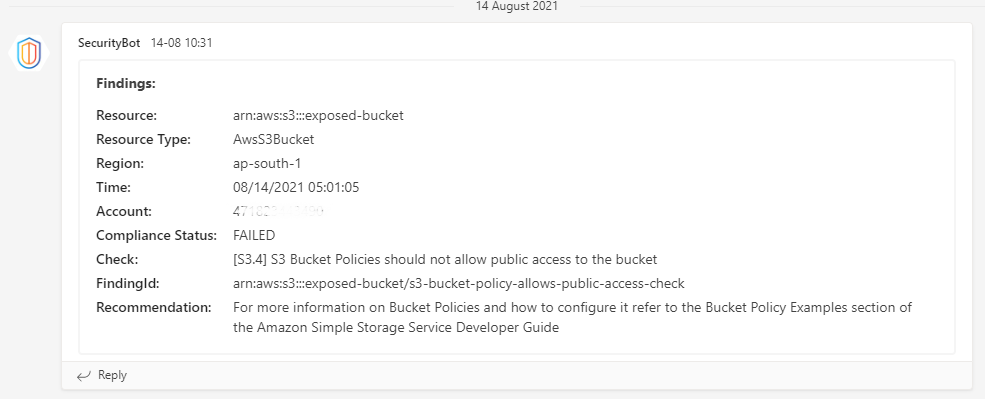
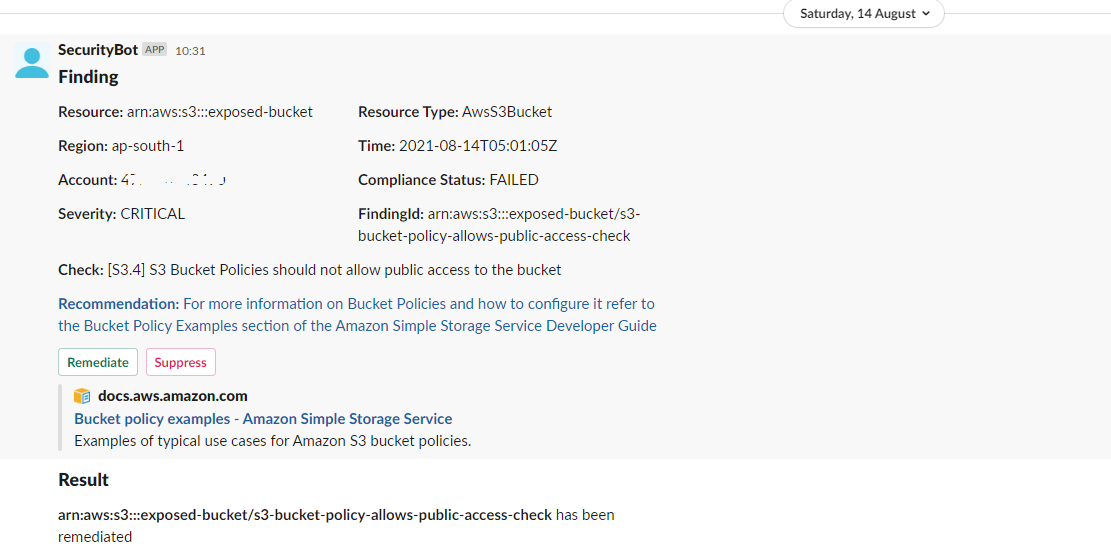
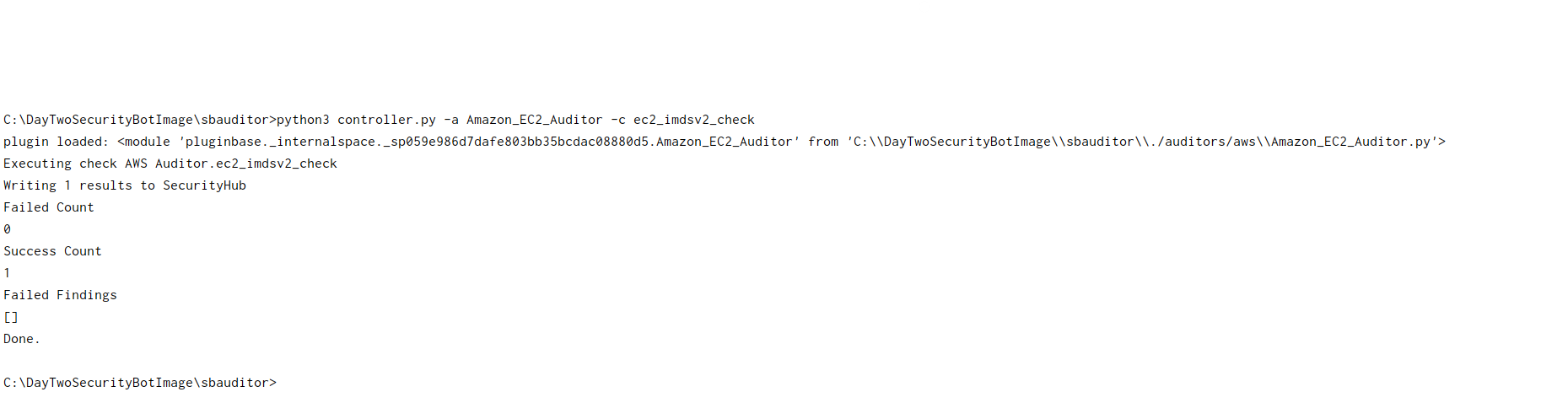
Using this to share, if we would like the same elsewhere lmk.
Side note: I'm open to writing the code for instance profile suggested with policy if we would like.
Need to digest why I'm getting the below when running tf apply. All else works fine prior and we verified https://docs.aws.amazon.com/cloud9/latest/user-guide/auth-and-access-control.html#auth-and-access-control-temporary-managed-credentials. As well the CLI works otherwise we could not have made ECS. Will look into this when I get a chance.
AWSReservedSSO_AWSAdministratorAccess_a63741ec6f766dc5:~/environment/ElectricEye/terraform-config-files (master) $ terraform apply -auto-approve
aws_cloudwatch_event_rule.Electric_Eye_Task_Scheduling_CW_Event_Rule: Refreshing state... (ID: electriceye-scheduler)
aws_vpc.Electric_Eye_VPC: Refreshing state... (ID: vpc-01abc8cddf44f7fe9)
aws_cloudwatch_log_group.Electric_Eye_ECS_Task_Definition_CW_Logs_Group: Refreshing state... (ID: /ecs/electriceye)
data.aws_caller_identity.current: Refreshing state...
aws_cloudwatch_log_group.Electric_Eye_FlowLogs_CWL_Group: Refreshing state... (ID: FlowLogs/electric-eye-vpc)
aws_ecs_cluster.Electric_Eye_ECS_Cluster: Refreshing state... (ID: arn:aws:ecs:us-east-1:162650249536:cluster/electric-eye-vpc-ecs-cluster)
data.aws_iam_policy.AWS_Managed_ECS_Events_Role: Refreshing state...
data.aws_availability_zones.Available_AZ: Refreshing state...
aws_s3_bucket.Electric_Eye_Security_Artifact_Bucket: Refreshing state... (ID: electriceye-artifact-bucket-us-east-1-162650249536)
aws_ssm_parameter.Electric_Eye_Bucket_Parameter: Refreshing state... (ID: electriceye-bucket)
aws_default_security_group.Default_Security_Group: Refreshing state... (ID: sg-0fcca8a97d731e1b6)
aws_subnet.Electric_Eye_Public_Subnets[1]: Refreshing state... (ID: subnet-0bd38eaf9530fe5cf)
aws_security_group.Electric_Eye_Sec_Group: Refreshing state... (ID: sg-046f662f39750d737)
aws_internet_gateway.Electric_Eye_IGW: Refreshing state... (ID: igw-076263f3fb9e1f7e0)
aws_subnet.Electric_Eye_Public_Subnets[0]: Refreshing state... (ID: subnet-06f28221aa7933ba9)
aws_route_table.Electric_Eye_Public_RTB[1]: Refreshing state... (ID: rtb-0718c9334c5045749)
aws_route_table.Electric_Eye_Public_RTB[0]: Refreshing state... (ID: rtb-06f019e345c048e82)
aws_route_table_association.Public_Subnet_Association[0]: Refreshing state... (ID: rtbassoc-0286e3233e5f44545)
aws_route_table_association.Public_Subnet_Association[1]: Refreshing state... (ID: rtbassoc-0ffb251239a5158e6)
aws_iam_role.Electric_Eye_ECS_Task_Execution_Role: Creating...
arn: "" => ""
assume_role_policy: "" => "{\n "Version": "2012-10-17",\n "Statement": [\n {\n "Sid": "",\n "Effect": "Allow",\n "Principal": {\n "Service": "ecs-tasks.amazonaws.com"\n },\n "Action": "sts:AssumeRole"\n }\n ]\n}\n"
create_date: "" => ""
force_detach_policies: "" => "false"
max_session_duration: "" => "3600"
name: "" => "electriceye-exec-role"
path: "" => "/"
unique_id: "" => ""
aws_iam_role.Electric_Eye_ECS_Task_Role: Creating...
arn: "" => ""
assume_role_policy: "" => "{\n "Version": "2012-10-17",\n "Statement": [\n {\n "Sid": "",\n "Effect": "Allow",\n "Principal": {\n "Service": "ecs-tasks.amazonaws.com"\n },\n "Action": "sts:AssumeRole"\n }\n ]\n}\n"
create_date: "" => ""
force_detach_policies: "" => "false"
max_session_duration: "" => "3600"
name: "" => "electriceye-task-role"
path: "" => "/"
unique_id: "" => ""
aws_iam_role.Electric_Eye_Scheduled_Task_Event_Role: Creating...
arn: "" => ""
assume_role_policy: "" => "{\n "Version": "2012-10-17",\n "Statement": [\n {\n "Sid": "",\n "Effect": "Allow",\n "Principal": {\n "Service": "events.amazonaws.com"\n },\n "Action": "sts:AssumeRole"\n }\n ]\n}\n"
create_date: "" => ""
force_detach_policies: "" => "false"
max_session_duration: "" => "3600"
name: "" => "electriceye-event-role"
path: "" => "/"
unique_id: "" => ""
aws_iam_role.Electric_Eye_FlowLogs_to_CWL_Role: Creating...
arn: "" => ""
assume_role_policy: "" => "{\n "Version": "2012-10-17",\n "Statement": [\n {\n "Sid": "",\n "Effect": "Allow",\n "Principal": {\n "Service": "vpc-flow-logs.amazonaws.com"\n },\n "Action": "sts:AssumeRole"\n }\n ]\n}\n"
create_date: "" => ""
force_detach_policies: "" => "false"
max_session_duration: "" => "3600"
name: "" => "electric-eye-vpc-flowlog-role"
path: "" => "/"
unique_id: "" => ""
Error: Error applying plan:
4 errors occurred:
* aws_iam_role.Electric_Eye_ECS_Task_Execution_Role: 1 error occurred:
* aws_iam_role.Electric_Eye_ECS_Task_Execution_Role: Error creating IAM Role electriceye-exec-role: InvalidClientTokenId: The security token included in the request is invalid
status code: 403, request id: 6d99ab49-839d-4bd2-a050-1450c41d6ef7
* aws_iam_role.Electric_Eye_Scheduled_Task_Event_Role: 1 error occurred:
* aws_iam_role.Electric_Eye_Scheduled_Task_Event_Role: Error creating IAM Role electriceye-event-role: InvalidClientTokenId: The security token included in the request is invalid
status code: 403, request id: 595dd7b1-bcda-4f7b-ba3c-e297cfc347f1
* aws_iam_role.Electric_Eye_ECS_Task_Role: 1 error occurred:
* aws_iam_role.Electric_Eye_ECS_Task_Role: Error creating IAM Role electriceye-task-role: InvalidClientTokenId: The security token included in the request is invalid
status code: 403, request id: f00bf274-f582-4997-bc25-4b352dc1c789
* aws_iam_role.Electric_Eye_FlowLogs_to_CWL_Role: 1 error occurred:
* aws_iam_role.Electric_Eye_FlowLogs_to_CWL_Role: Error creating IAM Role electric-eye-vpc-flowlog-role: InvalidClientTokenId: The security token included in the request is invalid
status code: 403, request id: cbfee016-6805-47c1-9bc2-0f9a04cce970
Terraform does not automatically rollback in the face of errors.
Instead, your Terraform state file has been partially updated with
any resources that successfully completed. Please address the error
above and apply again to incrementally change your infrastructure.