Comments to the U.S. CIO on Proposed HTTPS-Only Standard for Federal Websites
The CIO of the United States has proposed that all Federal government websites should support mandatory HTTPS encryption. The Open Technology Institute at New America wholeheartedly supports this proposal, which will significantly improve Americans’ privacy and security, and send a clear message that HTTPS protection should be considered a basic standard for all Web-based communications.
The websites of the Federal Government collectively house a vast quantity of important information about disability benefits, taxes, immigration, resources for veterans, Social Security, Medicare, workplace protections, and many other topics that may be highly personal in nature. Americans need and have a right to expect easy access to such information, and in the 21st century that means making these resources available on-line. However, there are many significant risks associated with providing digital access to such essential, sensitive, and frequently-accessed government resources in a manner that does not protect the security and privacy of those requesting them. By requiring Federal web sites to use HTTPS by default, agencies will be acting proactively to protect Americans as they conduct their day-to-day business with the Federal government, while also serving as an example for state and local governments to follow.
In the two decades since it was first released, HTTPS has become the global industry standard for securing private information as it travels across the Internet. Without HTTPS, many of today's most essential online services – ecommerce, online banking, digital medical record systems, etc. – would be unable to guarantee either the secrecy or the fidelity of the information they send to and receive from their users. Such guarantees are basic protections that consumers have every right to expect from all institutions that gather their personal and financial information. The U.S. CIO’s proposal would simply compel all Federal web sites to meet the level of service that Americans already expect and receive from the private sector.
HTTPS-enabled websites provide two critical protections over non-HTTPS sites: encryption and authentication. HTTPS encryption keeps the contents of a particular Web request or transaction secret, so that they cannot be accessed by anyone except the user and website exchanging the information. Even if the communication is intercepted by a third party, it will appear to be nothing but a jumble of random text. HTTPS authentication verifies that a website is actually associated with the person or organization it claims to represent, rather than by an impostor who set up the site to trick users into divulging personal information (known as a phishing attack). By adopting a policy of using HTTPS by default, a website gives its visitors confidence that the information they are getting is coming from the web site they intended to visit, and is exactly what that website intended to send them.
These protections are no longer seen as “optional” or only for “certain kinds of data” (traditionally limited to passwords, credit card numbers and little else). Indeed, encrypting all traffic on the Internet is increasingly seen as the only way for website owners to protect their users from diversion to imposter sites, or injection of malicious code. Recent research demonstrates that it is possible to infect a computer with malware by changing the contents of a legitimate but unencrypted website en-route. Additionally, this past month researchers discovered that non-encrypted traffic to common web sites is in fact already being altered en-route by foreign governments, in ways that have made visitors to these sites become unwitting contributors to distributed attacks on third-party websites.
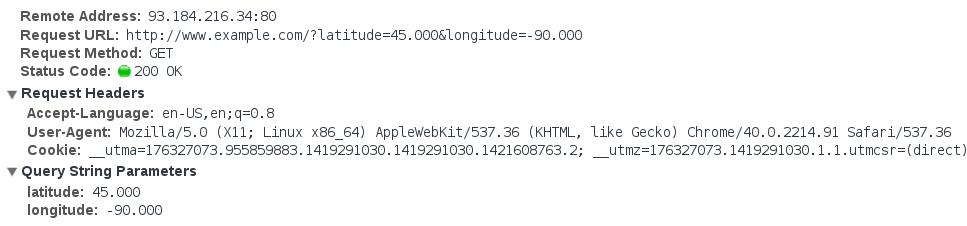
Without HTTPS, data sent between a website and any of its visitors can be recorded or manipulated by anyone who has access to any part of the network path between the two parties. For the many Americans who often access the Internet via free WiFi hotspots found in coffee shops, airports and city streets, the network path includes anyone who happens to be concurrently using the same WiFi access point. Many Americans also access the Internet from workplace and/or other institutional networks that are subject to comprehensive monitoring, a fact which can make it difficult or dangerous for users of the network to access a wide variety of important government resources. For example, researching OSHA violations from a workplace network could result in interrogation or retribution
Given the growing dangers associated with insecure Internet communications, it is more important than ever for Americans to know that traffic to and from U.S. Federal websites is not being intercepted, tampered with, or used as a vector for malware. The risks to personal privacy and security posed by a lack of universal support for HTTPS are significant, and the Federal government has both the means and the responsibility to lead the way in mitigating those risks.
The tools for implementing HTTPS support are widely available, the costs are minimal, and the best practices are widely documented, including by the government itself. What’s more, the cost of implementation will be particularly trivial for federal agencies since the government has already invested in all of the required infrastructure for creating secure certificates.
The U.S. CIO’s proposal brings the Federal government in line with well-established best practices in the tech sector, and is a privacy and security win for all Americans. Additionally, in adopting the CIO’s recommendations the Federal government will take a leading role in bringing more attention to the need for universal HTTPS adoption, and the importance of continuing to maintain and improve the standard’s underlying technologies. We strongly recommend the adoption of the HTTPS-only policy for Federal websites, and further encourage state and local governments to institute the same policy.
Jordan McCarthy, Staff Technologist ([email protected])
Nat Meysenburg, Staff Technologist ([email protected])
The Open Technology Institute at New America
1899 L Street NW, Suite 400
Washington, DC 20036