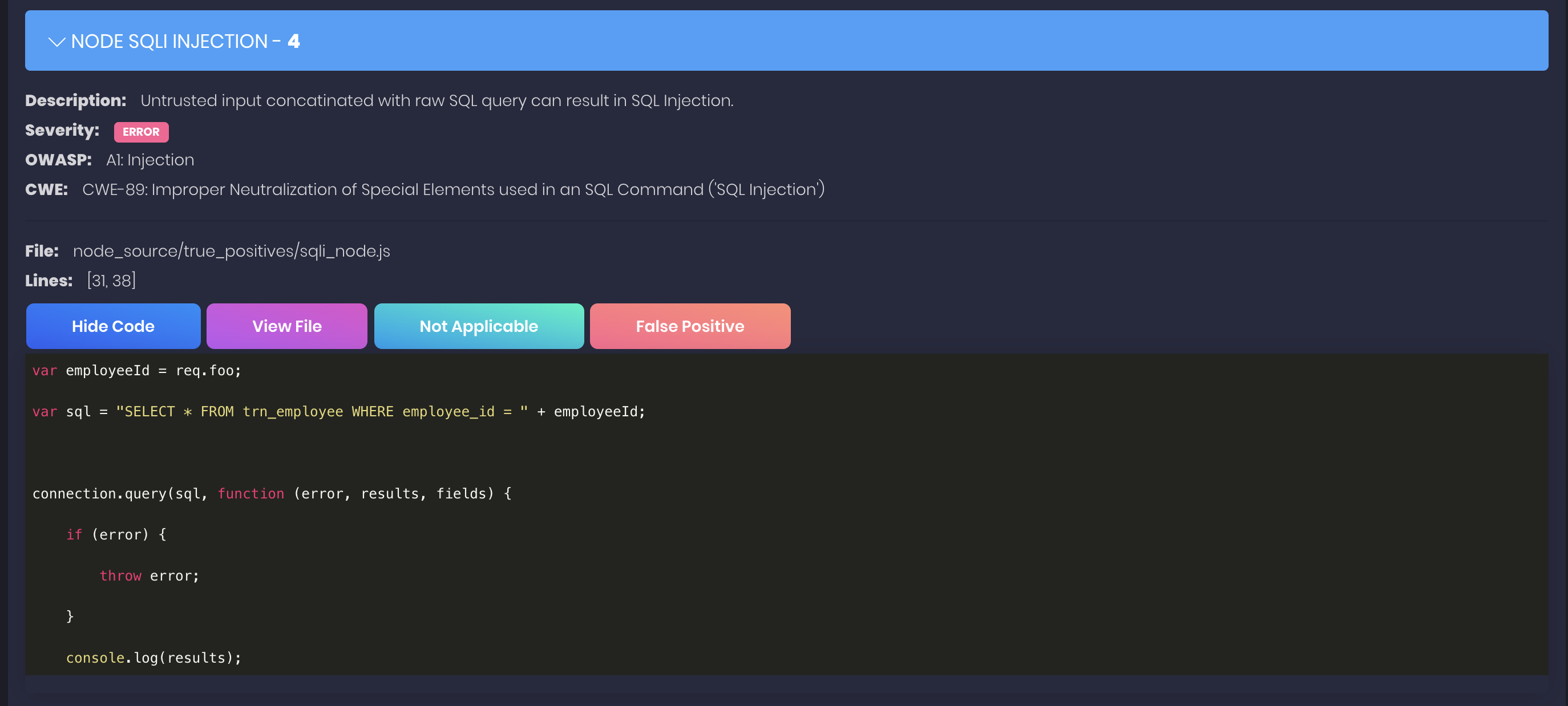
Static security code scanner (SAST) for Node.js applications powered by libsast and semgrep.
 OpSecX Node.js Security: Pentesting and Exploitation - NJS
OpSecX Node.js Security: Pentesting and Exploitation - NJS
docker pull opensecurity/nodejsscan:latest
docker run -it -p 9090:9090 opensecurity/nodejsscan:latestInstall Postgres and configure SQLALCHEMY_DATABASE_URI in nodejsscan/settings.py or as environment variable.
From version 4 onwards, windows support is dropped.
git clone https://github.com/ajinabraham/nodejsscan.git
cd nodejsscan
python3 -m venv venv
source venv/bin/activate
pip install -r requirements.txt
python3 manage.py recreate-db # Run once to create database schemaTo run nodejsscan
./run.sh
This will run nodejsscan web user interface at http://127.0.0.1:9090
- CLI: https://github.com/ajinabraham/njsscan#command-line-options
- API: https://github.com/ajinabraham/njsscan#python-api
Create your slack app Slack App and set SLACK_WEBHOOK_URL in nodejsscan/settings.py or as environment variable.
Configure SMTP settings in nodejsscan/settings.py or as environment variable.
- Github Action: https://github.com/ajinabraham/njsscan#github-action
- Gitlab CI/CD: https://github.com/ajinabraham/njsscan#gitlab-cicd
- Travis CI: https://github.com/ajinabraham/njsscan#travis-ci
docker build -t nodejsscan .
docker run -it -p 9090:9090 nodejsscan- CLI Docker Image: https://github.com/ajinabraham/njsscan#build-locally